September 26, 2019 by Siobhan Climer and Mishaal Khan
The number of sensitive records exposed in the first six months of 2019 reached a record 4.1 billion, already significantly higher than the total from 2018 – 126.7 million. That’s a 3136% increase in exposed records! While some of this increase is likely tied to improved breach identification, much is the result of methodical cyber criminals seeking valuable data assets.
 While the number of attack vectors has increased dramatically – think mobile and IoT – the types of attacks are much the same: malware, phishing, and DDoS. To combat these threats, businesses are at least outwardly making inroads in security investment.
While the number of attack vectors has increased dramatically – think mobile and IoT – the types of attacks are much the same: malware, phishing, and DDoS. To combat these threats, businesses are at least outwardly making inroads in security investment.
Unfortunately, security has historically been relegated to the backburner – and still is. Cybersecurity only accounts for 2% of IT expenditure, according to joint research by Canalys and ZDNet.
Here are some of the trends in security investment and management that businesses are making. Hopefully by investing more in protecting data, businesses will better protect their users and wallets.
Security Trends Of 2019
1. Compliance: GDPR, CCPA, and More
The General Data Protection Regulation (GDPR) is an EU law that protects data and consumer privacy. The law went into effect in May of 2018, and businesses around the world reeled from the implications. Despite its European focus, GDPR protects its citizens’ data around the world, so businesses everywhere were directly impacted.
Following on the heels of GDPR, California signed into law the California Consumer Protection Act (CCPA) in June of 2018. While both of these laws passed in 2018, the ramifications are more deeply felt this year as organizations respond to the first claims.
In the wake of these regulations, data residence awareness is increasing. It is still true today that many businesses do not know where their data is and how it transits from one location to another. GDPR, CCPA, and likely more state-by-state regulations in the coming months and years will hopefully change this.
See how information security and disaster recovery converge on the point of data protection in our latest point-of-view paper: The Crossroads of Data Protection.
2. Security Awareness Training
91% of cyber attacks begin with a spear phishing email, according to research from Trend Micro. Cyber criminals are smart and target the weakest security link: people.
The human factor is a notorious weak point in security architecture. In fact, according to Proofpoint, 99% of today’s cyber attacks are “human-activated.”
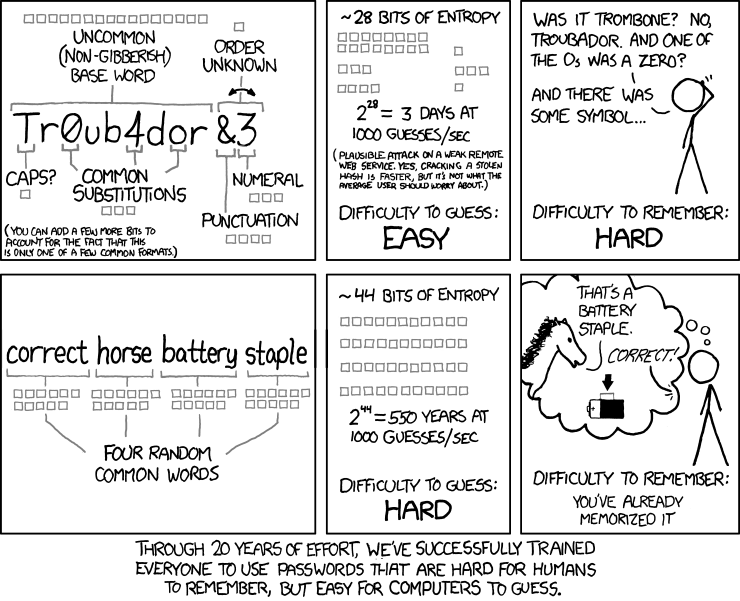
Security awareness training is, therefore, necessary. For security trends of 2019, users are receiving training in password hygiene, phishing detection, and security awareness. For example, here is a rather informative xkcd.com comic on the quantifiable benefit of a passphrase over a password.
3. Shut-Down Shadow IT
Users aren’t as reliant on IT to devise technology solutions as they were in previous eras. Generations that have grown up with the internet and constant access to technology are more confident troubleshooting their own issues – and finding solutions when needed.
Unfortunately, this means these users are more apt to bring in unverified applications and tools into your environment, creating an unmonitored realm of “Shadow IT”.
It is more important than ever for IT to be engaged in all aspects of the business. IT needs to inventory and monitor what users have access to and help them find the tools they need to solve for the problems of tomorrow.
4. Protecting Data In The Cloud And On-Premise
The data businesses rely on – and are tasked with protecting for their users and clients – no longer resides in a single data center. The use of laptops and mobile technology to access sensitive information, the rise of remote and  flexible work environments, and the use of cloud infrastructure to house data means data is everywhere.
flexible work environments, and the use of cloud infrastructure to house data means data is everywhere.
Protecting your businesses data – whether it is on-premise or in the cloud – is essential. Security experts ensure the data is protected by implementing multi-factor authentication, encryption, and tokenization to protect data both in transit and at rest. Emerging technologies will likely strengthen these protections in the coming years.
5. Managed Security
As the number of cyber attacks rises around the globe, it is more important than ever for businesses – whether they are a small local shop or international enterprise – to perform risk analysis and assessment to ensure they are secure from the most prevalent types of attacks.
Unfortunately, as report after report shows, there are almost 3 million open and unfilled cybersecurity positions around the world. And it’s getting worse. In 2015, 42% of organizations reported a problematic shortage of cybersecurity skills. Today, that number is up to 53%.
This is precisely why many SMBs and mid-market organizations work with managed services providers to bring in security experts who understand the big picture.
Experts like Mindsight.
Talk with our security experts today to learn how we can help you secure yourself against today’s threats.
Like what you read?
Contact us today to discuss the security trends of 2019.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
Strengthen Your Security Posture: Start With A Cybersecurity Framework



