June 12, 2018 by Siobhan Climer
As we recently reported, cybercrime damage costs are expected to double to $6 trillion over the next four years, according to Cybersecurity Ventures’ 2017 Official Cybercrime Report. Security is on the mind of every C-level and IT professional as they ask:
- How can we protect our mission-critical data?
- How can we ensure protection and detection layers of security are fully implemented?
- How do we remain agile and vision-forward without putting our business at risk?
CAMP IT Conferences
CAMP IT brings leaders in the industry together to try and answer these questions. CAMP IT began hosting conferences in 1984, informing IT professionals about emerging technologies. From IT Leadership and Digital Transformation Strategies to Business Intelligence, Analytics, and Big Data Strategies, CAMP IT connects the dots to help IT make critical decisions.
Risk management frameworks help bring visibility and data into the conversation, but  industry leaders are constantly looking to better understand their key business and compliance risks, how to prioritize resources, and how to add real value to business strategy development. Recently, several CSOs, CTOs, and VPs joined CAMP IT to learn about AI, cyber resilience, protection layer strategies, vendor risk management, and security risk management. The CAMP IT Mindsight Panel, led by Mindsight’s CTO and VP of Consulting Services, examined these very issues.
industry leaders are constantly looking to better understand their key business and compliance risks, how to prioritize resources, and how to add real value to business strategy development. Recently, several CSOs, CTOs, and VPs joined CAMP IT to learn about AI, cyber resilience, protection layer strategies, vendor risk management, and security risk management. The CAMP IT Mindsight Panel, led by Mindsight’s CTO and VP of Consulting Services, examined these very issues.
CAMP IT Mindsight Panel Examines Third Party Vendor Security
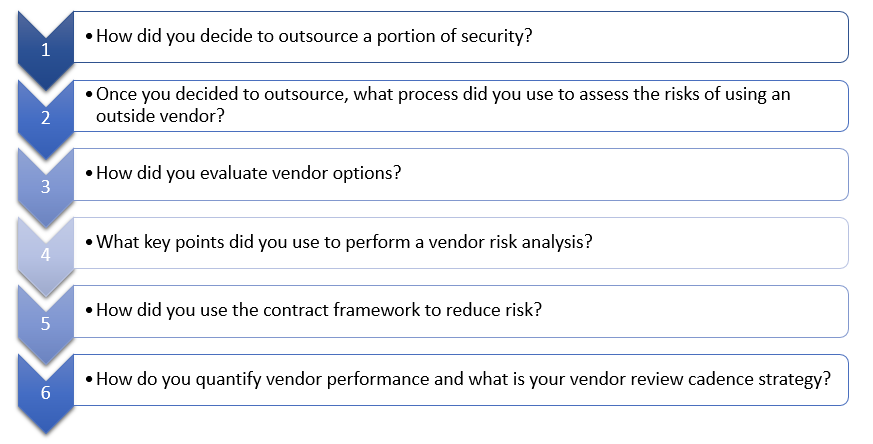
Mindsight Chief Technology Officer (CTO) and Vice President (VP) of Consulting Services, Jason Wankovsky, joined IT leaders in a recent CAMP IT Mindsight panel discussion to identify vendor selection frameworks, risk management strategies, vendor evaluations, and contract development. Almost 100 people gathered to listen to their thoughts on risk management. The engaging and energetic conversation quickly narrowed in on how to continuously assess risk when outsourcing security.
Jason Wankovsky led the panelist discussion on third-party vendor security. The conversation followed a chronological format, beginning with the decision to outsource a portion of security.
Interestingly, the conversation veered into the reliability and contractual framework early on, with much of the discussion both between the panelists and with the audience centering on trustworthiness. The panel and audience agreed that it is vital to determine if a vendor actually has what they say they have – whether that’s a product, skill, or capital – and how that then translates to sub-vendors.
The CAMP IT Mindsight panel provided some examples of the documentation you can receive as evidence. You need to be a thoughtful advocate for your enterprise and ask for certifications, case studies, exemplars, and documents that demonstrate the vendor can do what you need.
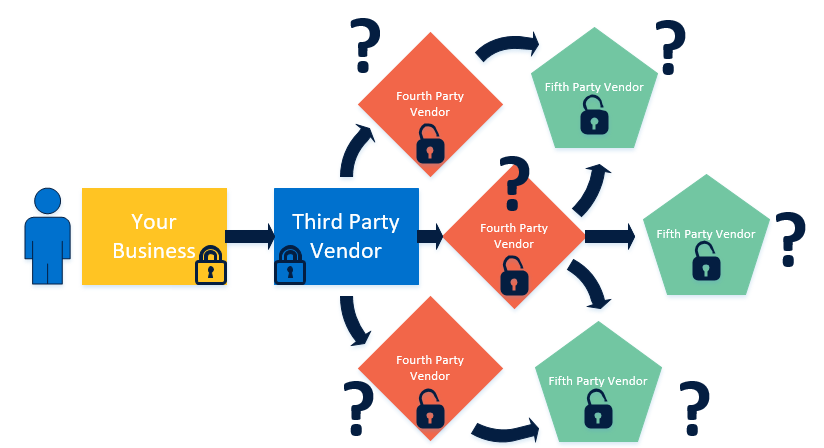
Beyond third party outsourcing, third-party vendors might partner with yet a different organization. These sub-vendors – fourth- or fifth-party vendors – are an important consideration in analyzing risk as well. Jason and the panelists observed that your chosen vendor should have already thought through your needs, identified additional vendor needs, and obtained the appropriate documentation.
In the diagram below, it is easy to see what might happen to your data when it leaves your hands. Be sure to have open lines of communication with your trusted third-party vendor and with whomever they partner.
The Right To Audit
Contract negotiations became a focal point in the conversation, with many audience members curious as to how they could utilize contracts effectively, ensure all risks are considered, and protect their enterprises’ most valuable assets. Jason and the panelists offered several ideas on how to make contracts work, such as ensuring all hardware, users, vendors, and services are covered through the contract. Other considerations mentioned were:
Service-level Agreement (SLA) Penalties – Ensure there are penalties in place in the event a vendor does not meet service agreements. Many SLAs include monthly credit penalties, where the service for the month is free if objective targets are not fully met. However, your enterprise is still left with the failed service. Onerous penalties should take into consideration the vendor’s culture and pain points. An effective penalty could be to have the CEO of the outside vendor perform an on-site visit to your organization. It all depends on the individual contractor; regardless, ensure these penalties are spelled out in the SLA.
Exit Clauses – What if the vendor fails to meet SLAs repeatedly? You do not want to be in a position where you are stuck with a risky vendor, which is why it is so important to include breach language in your agreements. You need to have an out for non-delivery so your business doesn’t fall behind because of third-party vendor failures. Identify how much room you feel it is appropriate to offer for delays or dishonored SLAs. Setting expectations like this early on ensures everyone knows what is flexible and what is rigid.
Right to Audit – No matter which vendor you choose or how many sub-vendors they collaborate with, ensure you have the right to audit them. If your IT service provider contracts with a cloud provider, make sure you have the right to communicate with that cloud provider. This enables you to maintain control of your project by staying informed and ensuring your business needs are met.
You Can’t Always Audit
One of the moments that stood out in the CAMP IT Mindsight Panel conversation was when discussing large public cloud options. The reality is you won’t be able to audit these top-of-the-industry providers. The question was then posed: How do you make public cloud options work? Jason and the panelists came to a unanimous decision that the rule of universal reliability applies. The number of vendors and enterprises and research and trust these public cloud options have engaged means they are reliable.
Mindsight’s Holistic Approach To Security
In the end, it is all about applying layers of security that achieve a maximum web of coverage. These solutions and services fall into two major categories: the Protection Layer and the Detection Layer.
The Protection Layer is comprised of tools designed to prevent penetration and “wall off” the environment. These come in the form of Firewalls, Advanced Firewall rules and software, and End Point Protection for both Malware and Anti-Virus, as well as tools for redirecting malicious DNS and URL activity to a safe landing, protecting users from themselves.
Unfortunately, there is no such thing as 100% secure or “hacker proof” unless you operate in an environment that is completely off the grid. This is where the Detection Layer comes in. The solutions and services deployed in the detection layer identify anything that gets through your protection measures. The tools Mindsight deploys are integrated with a 24/7 Security Operations Center (SOC) that monitors log activity, network traffic (both external and within the LAN (east-west)), and activity on web facing applications. The detection data is then correlated to provide actionable threat and breach intelligence in real-time, enabling a team to rapidly quarantine and remediate issues.
Roadmaps, Reliable Tech, And Expert Architects
Setting goals requires an honest assessment of where you are. By performing a roadmap assessment, you can understand where you are so you can figure out where you want to go. Mindsight offers multiple technology roadmaps and assessments that bring in our expert architects to identify and solve your unique business challenges. Security risk isn’t going away. The CAMP IT Mindsight Panel addressed this.
As Mindsight CEO and President Ed Kapelinski says, “Reality will come up and smack you in the head if you don’t pay attention to it.”
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Author
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.
How Emerging And Midmarket Companies Leverage Managed Services